[譯文] Bypass Information - CRC介紹
Q:CRC是神馬,能吃嘛!?
A:循環冗餘校驗(英語:Cyclic redundancy check,通稱「CRC」)是一種根據網路數據封包或電腦檔案等數據產生簡短固定位數驗證碼的一種雜湊函數,主要用來檢測或校驗數據傳輸或者保存後可能出現的錯誤。
下面是EMS的CRC介紹,覺得寫得還算完整就用本嫩嫩最強的技能Ctrl+C給貼過來拉~
順便翻譯下,翻譯就附在原文下囉,希望英文不好的可以趁機看看...
順帶一提...EMS跟TwMS的MSCRC基本上是一樣的喔...
來源:https://ccplz.net/threads/ems-v75-bypass-information.23009/
翻譯:KNowlet 技術の休閒
MSCRC
Addys:
地址(Address):
Finding those addys is easy.
How to find the MSCRC Addys yourself:
You will get the first MsCRC addy by debugging ANY addy between Maplestory start and end (Read). After that debug the adress that you found, and you will get the 2nd CRC addy. The third addy checks the main crc aswell.
That's all there is to it. Then apply the correct hooks and you're done with MSCRC. The problem is the HSCRC though.
這就是所有要做的啦。然後只要進行正確的修改,就搞定楓之谷的循環冗餘校驗了。問題出在駭盾(暫譯)的循環冗餘校驗上。
![[IMG]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_vrP8ufNVa6uHAMLD8hugtlzqIrvn9GWDgCqfY-OnekVoclursQZiMq8mdaMAcnxY7JfXFFQv0LbtL04yourWaX5WnCeO9DCqSTjZcQ-XNcPHFW6J-BLDVBtcW8Sbk=s0-d)
![[IMG]](https://lh3.googleusercontent.com/blogger_img_proxy/AEn0k_uesPJCEFklXxT5F3G9tpXCqXypzCQ4D9OFFLAzR13PrZ-dYkhfltmEs2Nv-_kR49gbXcVg52ETdHUIUUvnaAw9Tt3wEz9JvvMnI24GzJk1TGl0AT8Z138qPpQI4A=s0-d)
So the addys that you'd like to hook are probably 0x00AECE04 and 00FF15A9.
所以你可能會喜歡修改的位址應該是00AECE04和00FF15A9。
Now take a look at the first picture. You can see that it checks the addy that is in ecx.
So what we gonna do is hook at that addy and instead of the real ecx show MS CRC the same addy in our copied memory.
現在看一下第一張圖。你會看到檢測的地址在Ecx暫存器當中。
The explanation of this hook is in the other tutorial that i wrote and released in general programming. Go take a look if you don't understand what this does.
這個範例是我在其他教程中撰寫並發在一般的程式裡的(還是意思是說發佈給大眾?)。如果不懂在幹嘛就看看吧。
The second CRC will only control a small region around the other 2 CRCs.
This is how to bypass its check for the first crc addy:
第二個循環冗餘校驗只會檢測另外兩個的附近位置。
Same as first hook but only checks if edx is right next to MsCRC1, and then bypasses. If you're going to adjust the check-regions for the 3rd MsCRC addy, then be sure to use the correct range. If the range is too big this will crash your Maplestory.
如同第一個修改方法,但只檢測Edx暫存器是否正好在第一個楓之谷循環冗餘校驗,並繞過。如果要改檢測的值,請確認設定的範圍正確。如果範圍過大會導致楓之谷崩潰。
This was the whole MS CRC bypass for version 74.2 of Maplestory Europe and the versions before that. Now you gotta add the 3rd MS CRC addy and hook it and adjust the 2nd one to
check the 3rd addy aswell.
這就是如何繞過歐洲74.2版楓之谷循環冗餘校驗,和更早期的版本。現在你還要修改第三個校驗並修改第二個的值來檢測第三個的值。(我知道這邊翻得很爛QQ)
In order to bypass this check there have been 2 different public methods. The one was hooking OpenProcess. This could easily be done with OllyDBG for example.
After that method was patched there has been a new method that was working up to v74.2 of EMS:
要繞過這檢測有兩個公開的方法。其中一個是修改OpenProcess。這能以OllyDBG輕易地達成。在這方法被修好後有一個新方法一直活到歐洲74.2版楓之谷:
Making HackShield think that the user runs a 64 bit operational system so that hackshield won't load the important drivers. This has been patched as of v74.3 and v75.
讓駭盾(暫譯)認為系統是64位元就不會載入驅動。在74.3之後已被修復。
The new method is still private.
新的方法還未公開。
Hack Shield
駭盾(暫譯)
Hack Shield checks a lot of other stuff aswell. It checks like an Anti Virus programme, which would be checking a structure of a running process if it looks identical to something in the database, in this case an injector programme, a debugger programme, etc.
駭盾(暫譯)也檢測了一堆其他的東西。就像程式用的防毒軟體,他會檢查正在運行的進程,是否看起來像數據庫中的結構,例如注入器、調試器等等。
The new Hack Shield will also protect the MapleStory memory and the process. After Hack Shield loaded you can't inject anything into Maplestory with regular injecting methods. That's why VEH debugging won't work anymore, it needs to inject a .dll into the process that is being debugged.
新版本的駭盾(暫譯)會保護楓之谷的記憶體和進程。當駭盾(暫譯)載入後你無法再用正常方法注入任何東西進楓之谷。這就是為何VEH調試器沒辦法用了,需要注入一個DLL到要調試的進程裡。
A:循環冗餘校驗(英語:Cyclic redundancy check,通稱「CRC」)是一種根據網路數據封包或電腦檔案等數據產生簡短固定位數驗證碼的一種雜湊函數,主要用來檢測或校驗數據傳輸或者保存後可能出現的錯誤。
下面是EMS的CRC介紹,覺得寫得還算完整就用本嫩嫩最強的技能Ctrl+C給貼過來拉~
順便翻譯下,翻譯就附在原文下囉,希望英文不好的可以趁機看看...
順帶一提...EMS跟TwMS的MSCRC基本上是一樣的喔...
來源:https://ccplz.net/threads/ems-v75-bypass-information.23009/
翻譯:KNowlet 技術の休閒
MSCRC
Addys:
地址(Address):
Code (text):
unsigned long MsCRC1 = 0x00AECE06;
unsigned long MsCRC2 = 0x00FF15AB;
unsigned long MsCRC2 = 0x00FF15AB;
找到這些地址很簡單。
How to find the MSCRC Addys yourself:
如何靠自己找到這些楓之谷的校驗地址呢:
You will get the first MsCRC addy by debugging ANY addy between Maplestory start and end (Read). After that debug the adress that you found, and you will get the 2nd CRC addy. The third addy checks the main crc aswell.
對楓之谷循環冗餘校驗區段間任意地址下訪問斷點你會得到楓之谷第一個校驗地址,然後再對你所得到的地址下訪問斷點你可以得到第二個校驗地址。第三個地址檢測主要的循環冗餘校驗。
That's all there is to it. Then apply the correct hooks and you're done with MSCRC. The problem is the HSCRC though.
這就是所有要做的啦。然後只要進行正確的修改,就搞定楓之谷的循環冗餘校驗了。問題出在駭盾(暫譯)的循環冗餘校驗上。
Those addys above are the addys i got from debugging. Now you can hook the functions at this location, but most people prefer different locations.
下面這些地址就是我調試出來的。你可以直接修改下面的位址,但大多數人喜歡改其他位址。
下面這些地址就是我調試出來的。你可以直接修改下面的位址,但大多數人喜歡改其他位址。
So the addys that you'd like to hook are probably 0x00AECE04 and 00FF15A9.
所以你可能會喜歡修改的位址應該是00AECE04和00FF15A9。
Now take a look at the first picture. You can see that it checks the addy that is in ecx.
So what we gonna do is hook at that addy and instead of the real ecx show MS CRC the same addy in our copied memory.
現在看一下第一張圖。你會看到檢測的地址在Ecx暫存器當中。
所以我們要修改地址使暫存器有與楓之谷複製區段中相同地址有一樣的循環冗餘校驗數值。
(也可譯作:「所以我們要修改地址並以楓之谷複製區段中相同地址的循環冗餘校驗數值替換原本暫存器裡的值。」)
Code (text):
unsigned long MsCRC1 = 0x00AECE04;
unsigned long MsCRC1Return = MsCRC1+5;
//Maplestory Memory begin and end:
unsigned long Begin = 0x00401000
unsigned long End = 0x161a000 //last page, not necessary, you can use any page or even smaller number, but who cares :P
void __declspec(naked) MsCrcHook1()
{
__asm
{
cmp ecx,Begin
jl exit1
cmp ecx,End
jg exit1
sub ecx,Begin
add ecx,[MemoryCopy]
exit1:
mov dl,[ecx] //you have to adjust this if you're going to hook at a different location, these are the original opcodes that you write your jump on.
add dl,01
jmp [MsCRC1Return]
}
}
unsigned long MsCRC1Return = MsCRC1+5;
//Maplestory Memory begin and end:
unsigned long Begin = 0x00401000
unsigned long End = 0x161a000 //last page, not necessary, you can use any page or even smaller number, but who cares :P
void __declspec(naked) MsCrcHook1()
{
__asm
{
cmp ecx,Begin
jl exit1
cmp ecx,End
jg exit1
sub ecx,Begin
add ecx,[MemoryCopy]
exit1:
mov dl,[ecx] //you have to adjust this if you're going to hook at a different location, these are the original opcodes that you write your jump on.
add dl,01
jmp [MsCRC1Return]
}
}
這個範例是我在其他教程中撰寫並發在一般的程式裡的(還是意思是說發佈給大眾?)。如果不懂在幹嘛就看看吧。
Code (text):
//This is how we gonna hook:
MakePageWritable(MsCRC1 , 5);
Jump(MsCRC1 , MsCrcHook1, 0);
MakePageWritable(MsCRC1 , 5);
Jump(MsCRC1 , MsCrcHook1, 0);
This is how to bypass its check for the first crc addy:
第二個循環冗餘校驗只會檢測另外兩個的附近位置。
下面是如何繞過第一個檢測地址的方法:
Code (text):
unsigned long MsCRC2 = 0x00FF15A9;
unsigned long MsCRC2Return = 0x00FF0A45; //follow jump below
unsigned long CRCRegion1 = MsCRC1 - 6;
unsigned long CRCRegion2 = MsCRC1 + 6;
void __declspec(naked) MsCrcHook2()
{
__asm
{
cmp edx,CRCRegion1
jl exit2
cmp edx,CRCRegion2
jg exit2
sub edx,Begin
add edx,[MemoryCopy]
exit2:
push [edx]
jmp [MsCRC2Return ]
}
}
unsigned long MsCRC2Return = 0x00FF0A45; //follow jump below
unsigned long CRCRegion1 = MsCRC1 - 6;
unsigned long CRCRegion2 = MsCRC1 + 6;
void __declspec(naked) MsCrcHook2()
{
__asm
{
cmp edx,CRCRegion1
jl exit2
cmp edx,CRCRegion2
jg exit2
sub edx,Begin
add edx,[MemoryCopy]
exit2:
push [edx]
jmp [MsCRC2Return ]
}
}
如同第一個修改方法,但只檢測Edx暫存器是否正好在第一個楓之谷循環冗餘校驗,並繞過。如果要改檢測的值,請確認設定的範圍正確。如果範圍過大會導致楓之谷崩潰。
Code (text):
//This is how we gonna hook:
MakePageWritable(MsCRC2 , 7);
Jump(MsCRC2 , MsCrcHook2, 2);
MakePageWritable(MsCRC2 , 7);
Jump(MsCRC2 , MsCrcHook2, 2);
check the 3rd addy aswell.
這就是如何繞過歐洲74.2版楓之谷循環冗餘校驗,和更早期的版本。現在你還要修改第三個校驗並修改第二個的值來檢測第三個的值。(我知道這邊翻得很爛QQ)
HSCRC
The HSCrc checks the MS CRC. If it gets manipulated you will get either a "Hacking Thread Detected" or a "Memory Alteration towards Protection module detected".
駭盾(暫譯)的循環冗餘校驗檢測楓之谷的校驗。如果發現修改就會顯示「偵測到外掛」或「發現保護模組遭到修改」。
The HSCrc checks the MS CRC. If it gets manipulated you will get either a "Hacking Thread Detected" or a "Memory Alteration towards Protection module detected".
駭盾(暫譯)的循環冗餘校驗檢測楓之谷的校驗。如果發現修改就會顯示「偵測到外掛」或「發現保護模組遭到修改」。
In order to bypass this check there have been 2 different public methods. The one was hooking OpenProcess. This could easily be done with OllyDBG for example.
After that method was patched there has been a new method that was working up to v74.2 of EMS:
要繞過這檢測有兩個公開的方法。其中一個是修改OpenProcess。這能以OllyDBG輕易地達成。在這方法被修好後有一個新方法一直活到歐洲74.2版楓之谷:
Making HackShield think that the user runs a 64 bit operational system so that hackshield won't load the important drivers. This has been patched as of v74.3 and v75.
讓駭盾(暫譯)認為系統是64位元就不會載入驅動。在74.3之後已被修復。
The new method is still private.
新的方法還未公開。
Hack Shield
駭盾(暫譯)
Hack Shield checks a lot of other stuff aswell. It checks like an Anti Virus programme, which would be checking a structure of a running process if it looks identical to something in the database, in this case an injector programme, a debugger programme, etc.
駭盾(暫譯)也檢測了一堆其他的東西。就像程式用的防毒軟體,他會檢查正在運行的進程,是否看起來像數據庫中的結構,例如注入器、調試器等等。
The new Hack Shield will also protect the MapleStory memory and the process. After Hack Shield loaded you can't inject anything into Maplestory with regular injecting methods. That's why VEH debugging won't work anymore, it needs to inject a .dll into the process that is being debugged.
新版本的駭盾(暫譯)會保護楓之谷的記憶體和進程。當駭盾(暫譯)載入後你無法再用正常方法注入任何東西進楓之谷。這就是為何VEH調試器沒辦法用了,需要注入一個DLL到要調試的進程裡。
A simple check is: IsDebuggerPresent(). You can simply hook this Windows API and always return false.
一個最基礎的檢測是IsDebuggerPresent()。你可以修改這個API並使他一直回傳否。
ChiLaX, Aug 25, 2011
耶~終於翻譯完了 :)))
有錯的地方拜託跟我講一下,翻譯很爛就別尻我了QQ
目前的HS還有多開檢測和記憶體屬性保護,讓我們調用VirtualProtect失敗進而使記憶體無法修改。
一個最基礎的檢測是IsDebuggerPresent()。你可以修改這個API並使他一直回傳否。
ChiLaX, Aug 25, 2011
耶~終於翻譯完了 :)))
有錯的地方拜託跟我講一下,翻譯很爛就別尻我了QQ
目前的HS還有多開檢測和記憶體屬性保護,讓我們調用VirtualProtect失敗進而使記憶體無法修改。
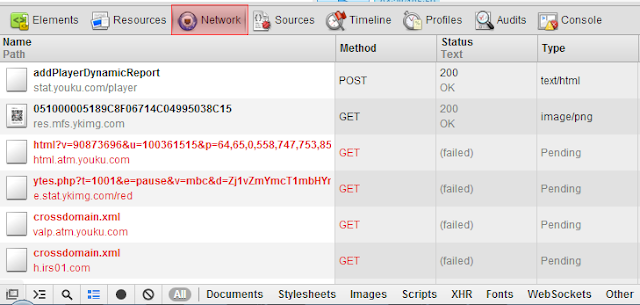
我怎麼都沒弄出第三個校驗地址 0.0
回覆刪除TwMS貌似沒有?
刪除好像是...
刪除如果再加一個就更煩了 =口="
Albert大大,請教一下如果要學寫MS多開程式,有推薦哪篇文張和程式嗎^^??
刪除大陸教程不錯
刪除想請問一下大大
回覆刪除你的程式基礎是再怎麼開始學的
是自學嗎?還是有去上課?
原本是因為想要改雙開上網找資料結果發現這個網站感覺蠻多寶可以挖的
只是敗在沒有程式的知識...
順便想要找個東西來學一學充實一下自己((春節有點無聊= ="
以上是我的問題
謝謝大大
主要是自學,學好玩或方便學VB就夠玩了,不然建議直接學C++或其他
刪除恩..VB是指VitualBox嗎?
刪除應該是指Visual Basic,微軟最早開發來寫Basic基礎程式語言的軟體。
刪除安安 大大你好我有一些外掛想要問您不知是好可以指導一下? rc:monkey92105 即時:mike92105
回覆刪除